-
 Encontrar enMiembros
Encontrar enMiembros Encontrar enVideos
Encontrar enVideos Encontrar enCanales
Encontrar enCanales
This website uses cookies to ensure you get the best experience on our website.
To learn more about our privacy policy haga clic aquíPreferencia de privacidad
Blogs Inicio
» Tecnología
» Secure Your App Now: Implement 2-Factor Authentication in Spring Webflux with This Essential Step-by-Step Guide!
-
- Última actualización 22 de octubre de 2024 0 comentarios, 98 vistas, 0 likes
More from Ava Parker
More in Politics
Related Blogs
Archivo
Secure Your App Now: Implement 2-Factor Authentication in Spring Webflux with This Essential Step-by-Step Guide!
Publicado por Ava Parker
22 de octubre de 2024
Cuerpo
In the current digital environment, multi-factor authentication (MFA) has become a crucial practice for many applications, especially those managing sensitive information like financial services. Additionally, MFA is increasingly required by law in various sectors within the EU, making it vital for developers to integrate this security feature into their applications. If you are developing an application that necessitates two-factor authentication, this article is a valuable resource.
In this piece, I will walk you through the steps to implement a two-factor authentication system for a reactive API created with Spring Webflux. This application employs TOTP (time-based one-time passwords generated by an app on the user's device, such as Google Authenticator) as the second layer of security, alongside traditional email and password combinations.
Understanding Two-Factor Authentication
From a technical perspective, two-factor authentication (or multi-factor authentication) is a security method that requires users to present two or more verification elements. Typically, this means a user must enter a password along with another form of identification. This second identifier can be a one-time password, hardware tokens, biometric data (like fingerprints), or other verification methods.
The two-factor authentication process includes several essential steps:
- The user inputs their email (or username) and password.
- Along with their credentials, the user provides a one-time code generated by an authenticator app.
- The application verifies the email (or username) and password, and checks the one-time code using the user's secret key issued during registration.
Using authenticator apps (such as Google Authenticator, Microsoft Authenticator, or FreeOTP) presents several benefits over SMS-based code delivery. These apps are less vulnerable to SIM attacks and can operate without cellular or internet access.
A Practical Example
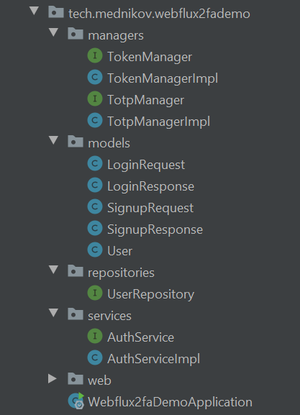
In this article, we will create a straightforward REST API that implements two-factor authentication methods. This API will require users to enter both an email-password combination and a short code generated by an app. You can utilize any compatible app to generate TOTP; for this demonstration, I will use Google Authenticator on Android. The source code is available in this GitHub repository. The application requires JDK 11, Maven, and MongoDB for user profile storage. Let’s examine the project structure in detail.
For more information on enhancing security with two-factor authentication, visit [this guide](https://t8tech.com/it/data/boost-security-with-2-factor-auth-in-spring-webflux-a-step-by-step-guide/).
In this piece, I will walk you through the steps to implement a two-factor authentication system for a reactive API created with Spring Webflux. This application employs TOTP (time-based one-time passwords generated by an app on the user's device, such as Google Authenticator) as the second layer of security, alongside traditional email and password combinations.
Understanding Two-Factor Authentication
From a technical perspective, two-factor authentication (or multi-factor authentication) is a security method that requires users to present two or more verification elements. Typically, this means a user must enter a password along with another form of identification. This second identifier can be a one-time password, hardware tokens, biometric data (like fingerprints), or other verification methods.
The two-factor authentication process includes several essential steps:
- The user inputs their email (or username) and password.
- Along with their credentials, the user provides a one-time code generated by an authenticator app.
- The application verifies the email (or username) and password, and checks the one-time code using the user's secret key issued during registration.
Using authenticator apps (such as Google Authenticator, Microsoft Authenticator, or FreeOTP) presents several benefits over SMS-based code delivery. These apps are less vulnerable to SIM attacks and can operate without cellular or internet access.
A Practical Example
In this article, we will create a straightforward REST API that implements two-factor authentication methods. This API will require users to enter both an email-password combination and a short code generated by an app. You can utilize any compatible app to generate TOTP; for this demonstration, I will use Google Authenticator on Android. The source code is available in this GitHub repository. The application requires JDK 11, Maven, and MongoDB for user profile storage. Let’s examine the project structure in detail.
For more information on enhancing security with two-factor authentication, visit [this guide](https://t8tech.com/it/data/boost-security-with-2-factor-auth-in-spring-webflux-a-step-by-step-guide/).










Comentarios